Improve Your Application’s Mobile Security with Tools and Determination
We carefully lock our houses and cars, may even have our laptops hard-wired to the internet (through a router, of course). Men keep their wallets in a front pocket and women hold their purses in front and close. We shred important documents, read our credit card and bank statements carefully. So, we’ve got the security issue nailed, right?
Probably not, if you carry a smart phone or other smart device. Recent research from Arxan determined that among the top paid and free mobile applications:
- 100% of the top 100 paid apps on the Google Android platform had been hacked
- 56% of the top 100 paid apps for Apple iOS had been hacked
- 73% of popular free apps on Android had been hacked
- 53% of popular free apps on Apple iOS had been hacked
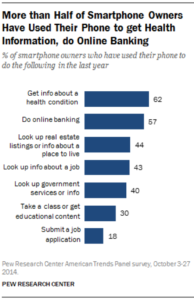
In addition, we’re using these devices freely to do things that expose our most personal data to hackers’ eyes. Check out these statistics from Pew.
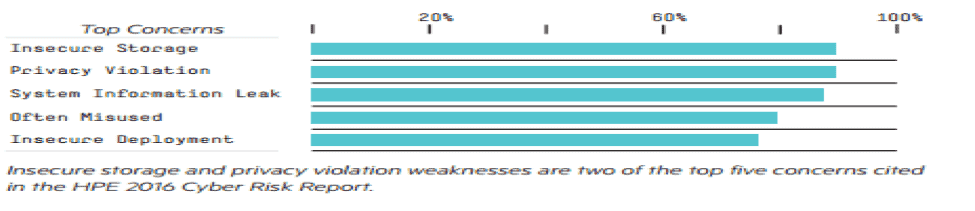
Gartner has reported that 75% of mobile apps can’t pass a basic security test and an HP study shows that the majority can access external storage as well. Most include logging methods. See the top concerns reported below.
So, what can a mobile app developer do to make things a lot better? First, find tools that help you detect and close security ‘holes’. Ensure the apps can’t easily be reverse-engineered or tampered with. Still, all it takes is one bad app on a device to expose all of your data. You also must secure your device. Data encryption and remote device wiping can be good strategies to protect sensitive data, but you have to know what data is really sensitive—what is the PII (personally identifiable information). Consider who needs what transactions and restrict the ones accessing critical data to only those who really need to get to that data to do their jobs.
The following blog, posted by Sarah Vonnegut in 2015 is still valuable information for developers.
15 Best Practices for Mobile Application Security:
- Do NOT store PII or other sensitive data on the user device
- Do NOT rely on built-in key chains
- Do practice defense in depth using the types of application security testing best suited for your budget and needs. SAST testing is especially critical here, as reviewing the source code is the best way to find flaws as early in the SDL/SDLC as possible.
- Do limit permissions to only the most necessary components required for the app to function correctly
- Do implement proper TLS by ensuring HTTPS is always used. Keep in mind how vulnerable your consumer will be on wi-fi networks.
- Do NOT hard-code data within the app
- Do invalidate a user’s session upon logout – on both the client and server side. Additionally, always log users out after a certain amount of inactive time in the application
- Do implement OAuth 2.0 where possible to reduce the chance of attackers performing man-in-the-middle attacks
- Do know which regulations your application needs to adhere to (PCI-DSS, HIPAA, etc.) and ensure that these are being addressed in the design stage.
- Do understand the nuances of each platform you’re developing for, whether it’s iOS, Android, or Windows
- Do ensure proper session management
- Do define trust boundaries
- Do use proper binary protection to combat buffer overflow and stack overflow attacks, along with jailbreaking
- Do understand what data will be collected and let that steer your security steps
- And finally – Do whatever is in your power to keep your mobile app consumer’s – whether employees or customers – data secure and trust intact.
From “Mobile Application Security 15 Best Practices for App Developers”
By Denise P. Kalm